How to Clean a Hacked WordPress Site!
Getting your site hacked is really a painfull thing, and if you are reading this probably your WordPress site got hacked. The first thing you need to do is don’t get panic. The first thing you need to do is don’t get panic and check if you have a backup of your WordPress website.
Be calm and let see how we can get your site back to normal. Since WordPress can be really hard for non-technical people to understand because with a lot of plugins installed we get confused that when and where are malicious files.
So we first need to identify malicious files, delete if the file is not a part of WordPress core, and make sure everything is in order. Let see that how we can clean a hacked WordPress site step by step.
Note: Don’t panic at all, try to follow these steps accordingly and hopefully everything will get back to normal. If you need help please contact us through the contact us form.
Step 1: Download Original WordPress!
As a first step, you need to download original WordPress so that you can compare what additional files you have in your WordPress installation. An original download can also help you to upload default files if one is corrupted in your installation.
You can download original WordPress from here.
Step 2: Upload Original Files in Home Directory!
Next step towards cleaning your site is to delete all files in your home directory and upload the defaults. Following image shows the default files of WordPress installation:
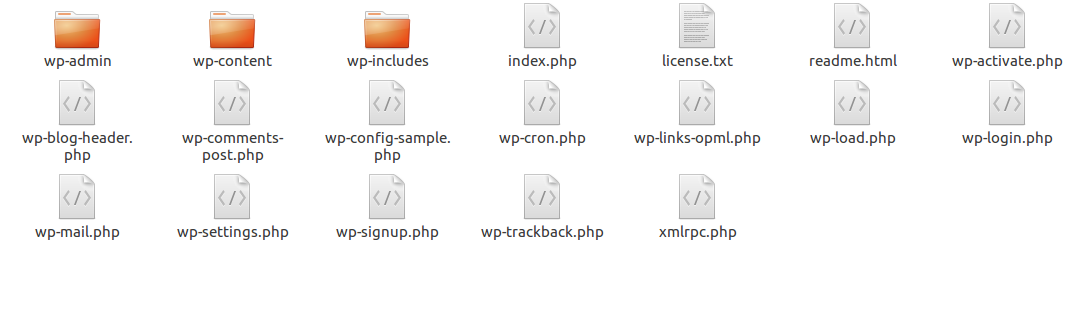
These are your default WordPress files, if you see any additional files in your installation it means that file is uploaded by a hacker. In the image below you can see 3 additional files one of them is a folder.
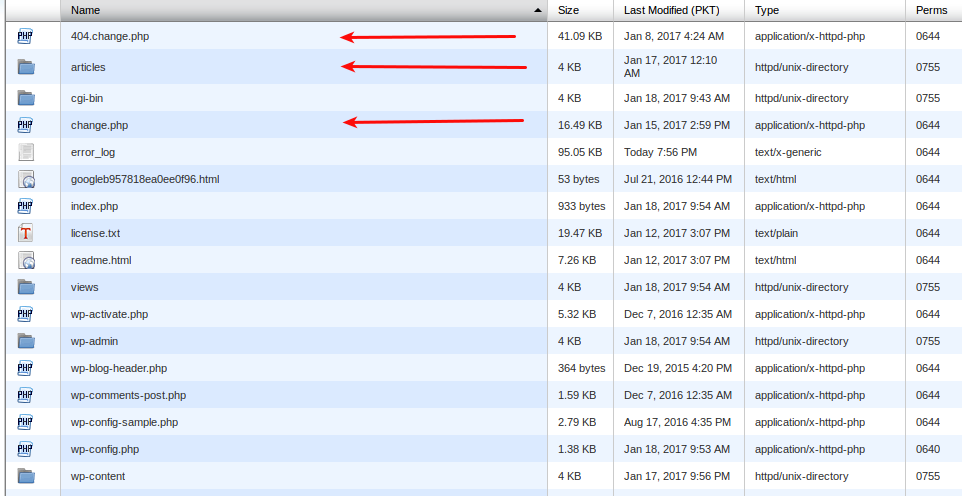
- 404-change.php
- change.php
- articles (folder)
These three files/folders are not present in default WordPress download, so you can confidently delete them. For now take a backup of your “wp-config.php” file and delete all files in home directory. Only delete files do not delete any folder yet.
Your home directory should only have following folders for now:
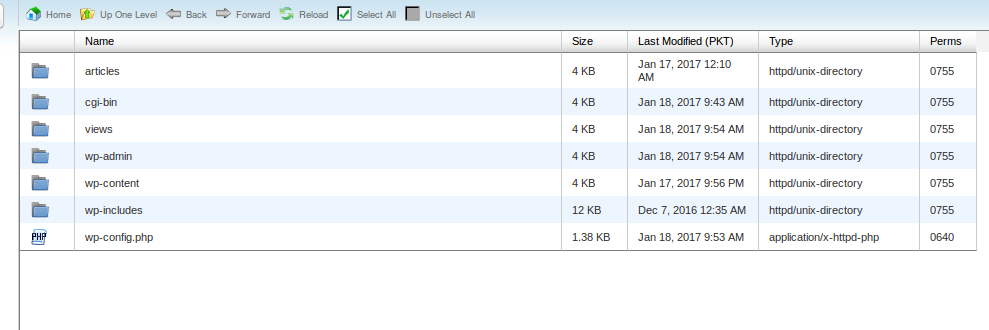
I’ve deleted all files except “wp-config.php”, now upload all files from the original WordPress download. You have just cleaned the default folder of your WordPress, but your installation is not yet fully cleaned.
Step 3: Clean wp-config.php file
It’s time we should clear the wp-config file, it may or may not be affected. You can open this file and see if it is affected or not, the content of “wp-config.php” file at my end looks like this:

You can clearly see that code shown in the image is injected by the hacker, you can do two things:
- Delete the unwanted code from this file.
- Or completely replace this file with the file present in core WordPress download.
Deleting unwanted code!
After deleting unwanted code your config file should look like this:
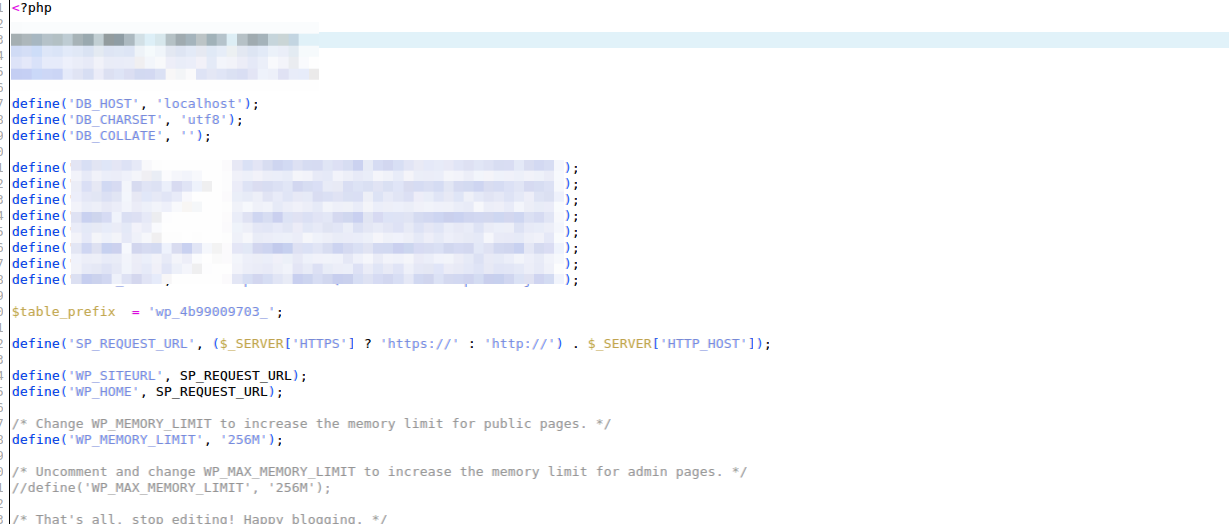
I’ve just blurred out the part which contains the database login details.
Completely Replace the WordPress file!
If you don’t want to delete the unwanted code, you can also replace it with the file present in WordPress original download. Just copy the database credentials from your old “wp-config.php” file and paste it in the file present in WordPress original download and simply upload this new file.
Step 4: Delete All Plugins!
Most of the time WordPress gets hacked by poorly written plugins, so before moving forward we need to delete all the installed plugins. Deleting plugins will not affect your WordPress installation.
All the plugins are located in this folder: wp-content/plugins
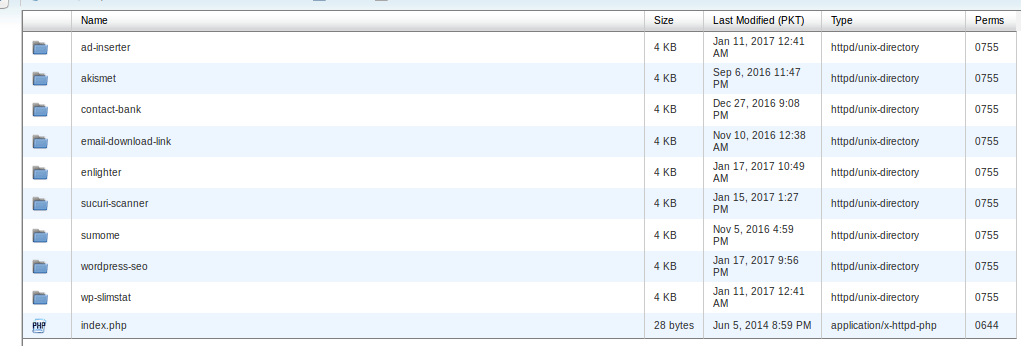
Currently, there are 9 plugins installed, you can delete all these folders and plugins will be removed from WordPress installation. After deleting all plugins your plugins folders should look like:
Even after deleting WordPress plugins WordPress installation is still not completely cleaned.
Step 5: Delete all unused themes!
Outdated themes are also mostly the cause of WordPress being hacked. So let us delete the unused themes. All the WordPress themes are located at “wp-content/themes”
Now at this step, you must know the name of your theme, otherwise, you might end up deleting the theme your site is using. 🙂 From themes folder delete all the themes except the one being used.
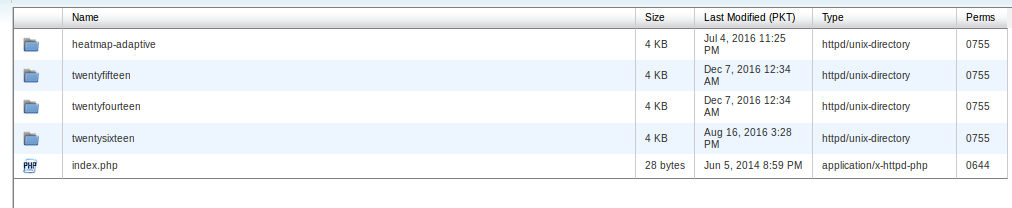
These are the themes installed on the site I am cleaning, I will delete all except the one being used after deletion theme folder should look like:

Now If you was not able to access your WordPress previously you should be able to at least access your WordPress installation and log in to the administration area.
If you are still not able to access administration area please contact us.
Step 6: Check Access Logs!
Checking access logs can give you a lot of information, you can do this step at the start or after performing all the above-mentioned steps. By checking access logs you can see what files are being executed on the server and see do they belong to WordPress core?
When I checked the access logs I see one IP trying to access “wp-login.php” page, it looks like a brute-force password attack.
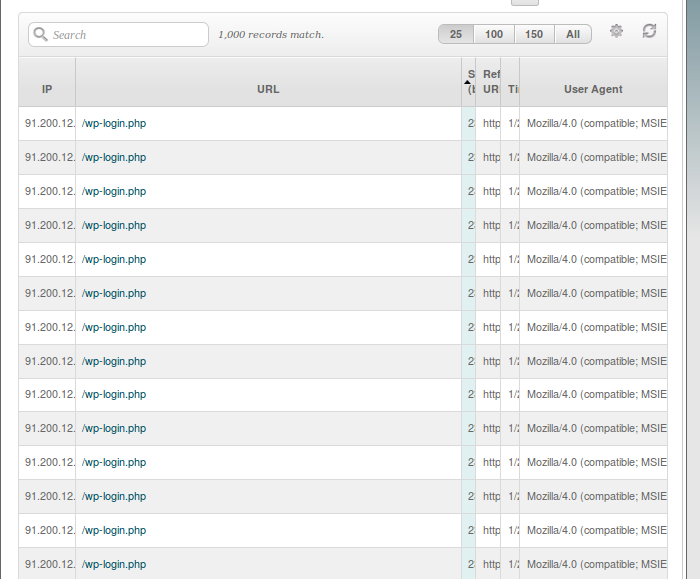
Actually, there was couple hundred of access to this page, which clearly states that someone is trying to enter your administration area.
On another instance someone was trying to access the pages that do not belongs to WordPress:
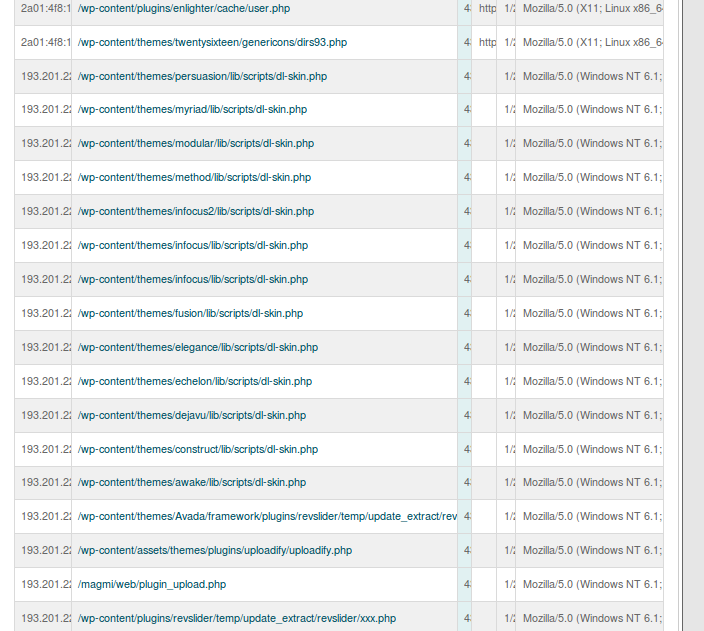
I then have to individually check these files and check if they are present in actual WordPress if they are not you can easily delete them as soon as possible, because these are the files hacker might be using to re-gain access once you try to clean your hacked WordPress.
You should not ignore checking access logs because as you can see they can tell you a lot about the hacker activity on your server. You can even completely remove all the malicious files by only looking at your access log activity.
Step 7: Scan your WordPress with WordFence!
I’ve tried couple many plugins but WordFence is one of the best, but before using WordFence make sure you have performed all the above-mentioned steps.
Now for remaining malicious files (if any), you can use WordFence to report them to you, you can either delete the reported files or remove malicious code inside them.
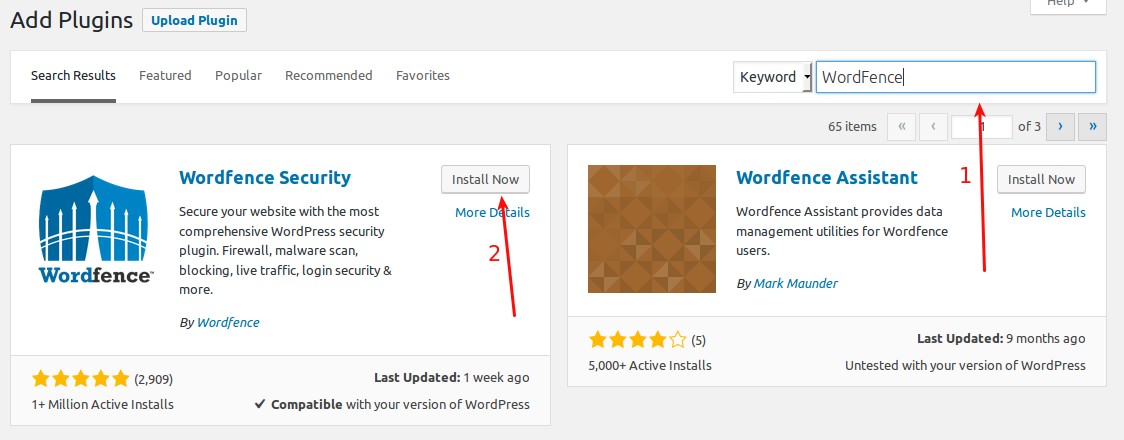
Just click “Add New” under Plugins in your WordPress, then put “WordFence” in the search bar, then “Install Now” to install the WordFence Plugin.
Perform a WordFence Scan
It is time we perform a WordFence Scan of your WordPress installation.
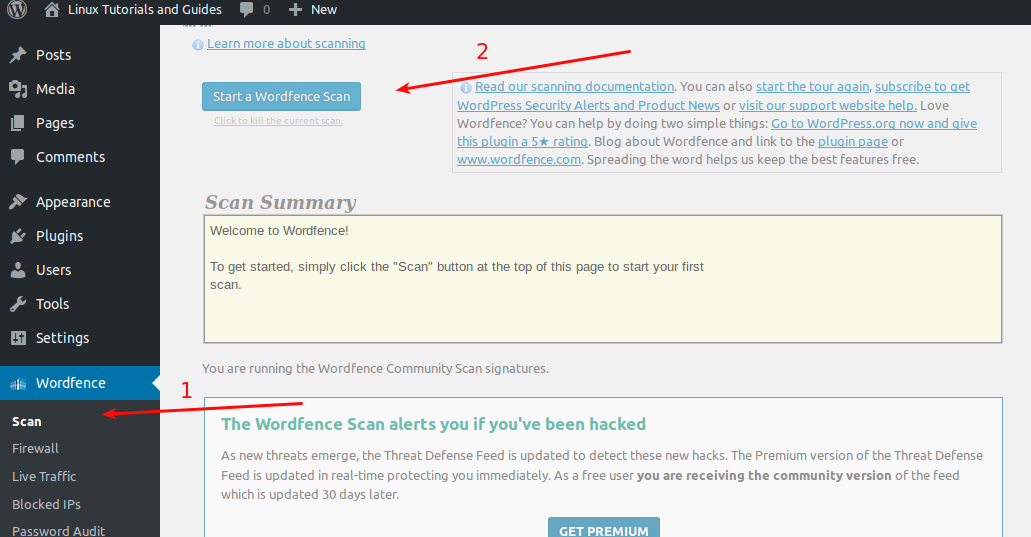
After the scan is finished you can scroll down to see the report of the scan if it says there are no threats than you are good, otherwise, you should be presented with report something like this:
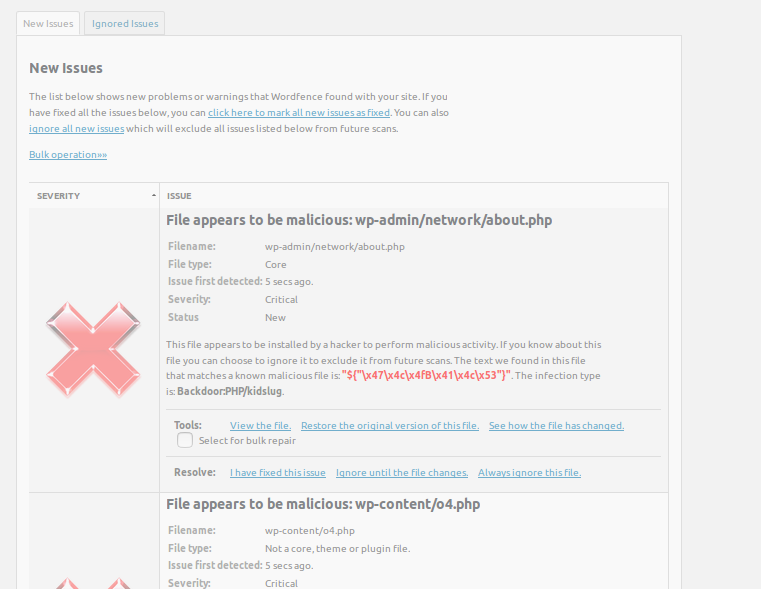
There will be a couple of reported files, you need to either delete these files or clean them once you have cleaned all the files reported by WordFence it would be fine to say that you have successfully cleaned your WordPress installation.
You can also use WordFence to repair these files for you, but I would recommend looking at them one by one manually.
WordFence Live Traffic
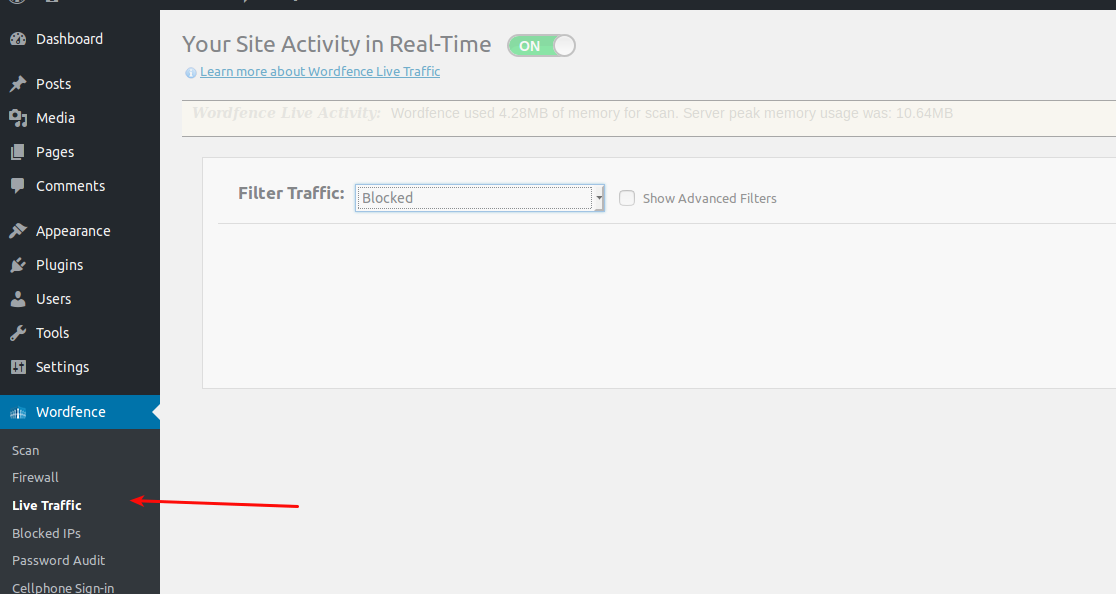
Once WordFence is installed you won’t need to rely on any other tool to look at your web traffic logs, you can use WordFence live traffic tool to track the traffic in real time. You can see:
- Human Traffic
- Blocked Traffic
- Bots
- Crawlers
Where to go from here?
I hope that by now you must have a clean WordPress site, if still not you can contact us. But you might have a question what to do after cleaning your site? It might get hacked again. However, you can be pro-active and prevent your site from getting hacked by doing following steps mentioned below.
Following Articles Could be Helpfull
5 Steps to secure newly installed web server
WordPress Security Through Logging & Audit Trail
How to install and configure ModSecurity on cPanel/WHM! (If you are using cPanel/WHM)
Use Web Application Scanner
You can be proactive by using a web application scanner to find the vulnerable code in your application or particularly in the case of WordPress you can scan WordPress site for vulnerable plugins because as I mentioned above plugins can be the entry point for hackers.
You can install easy to use desktop application from NetSparker, and scan your web application for the vulnerable code. If you still need any help feel free to ask questions in comments or contact us directly.